About Lev Lafayette

Lev Lafayette has an MHEd from Otago University, an MSc (Information Systems) from Salford University, and an MBA (Technology Management) from the Chifley Business School, where he was on the Dean's List. He also has a Graduate Certificate in Project Management from the same institution, and an honours degree from Murdoch University in Politics, Philosophy and Sociology which is commented upon by the Vice-Chancellor of the time. Many years later he completed a Graduate Certificate in Adult and Tertiary Education at the same institution. He also has a Graduate Diploma in Applied Psychology at the University of Auckland, and has recently finished a Master of Climate Change Science and Policy at the Victoria University of Wellington.
He is a certified PRINCE2 Practioner, and an Adult and Workplace Trainer. Clearly not satisfied with three masters degrees, he's started a fourth, this time a Master Climate Change Science and Policy at the Victoria University of Wellington. With an interdisciplinary approach, Lev's interests include the political implementation of universal pragmatics, the relationship between communications technology and society, and comparative economic systems. On again and off again, he plods his way through completing a PhD in Social Theory as well.
Professionally however, Lev is an experienced systems administrator, specialising in the Linux operating system and scientific applications, a project manager, systems engineer, and quality management systems coordinator, specifically for ISO 9001 (Quality assurance) and ISO 270001 (Information Technology Security). He also does a lot of training for researchers and technical staff in Linux, High Performance Computing, mathematical programming, Postgresql, and related subjects, with graduates and post-doctoral researchers from a variety of organisations including: RMIT, La Trobe University, the University of Melbourne, Deakin University, Swinburne University, Victoria University of Technology, Monash University, the Australian Synchrotron, the Department of Environment and Primary Industries, the University of Sydney, Macquarie University, the University of New South Wales, the University of Western Australia, the Australian Institute of Health Innovation, the Westmead Millennium Institute, the Australian Radiation Protection and Nuclear Safety Agency, and the Australian Institution of Marine Science.
Previous employment and clients include several years working as a computer systems trainer and database management for the Parliamentary Labor Party in Victoria. Following this he worked for the Ministry of Foreign Affairs in Timor Leste (East Timor) managing their computer network and providing training and technical expertise to that Ministry in their first year of self-governance. Dr. Ramos-Horta provided the following comments on his work.
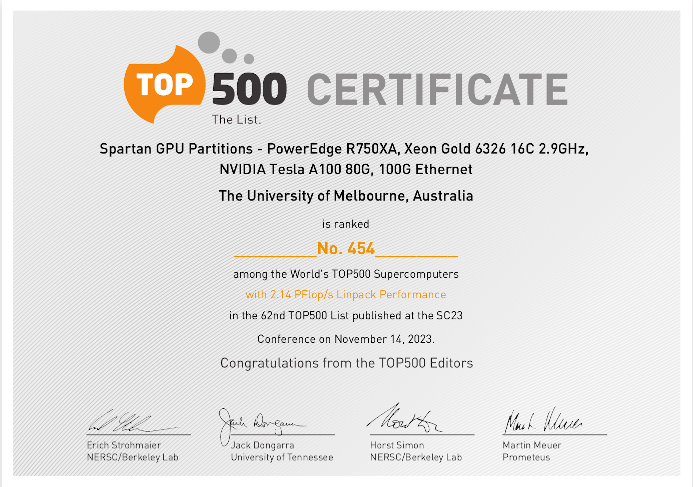
Lev works for the Research Computing Services group at the University of Melbourne as the Senior High Performance Computing Development and Operations Engineer, and prior to that Victorian Partnership for Advanced Computing, as a systems administrator for Linux clusters and as the Quality Management Coordinator. As per those roles, this site is mostly dedicated to issues concerning High Performance Computing, Scientific Computing and Supercomputing. Lev is involved in Linux Users of Victoria, having spent four years as President, two years as Public Officer, two years as Vice-President, a year as Treasurer and is now in his third year as an ordinary committee member. He is has a coordinating role in the annual Multicore World conference and typically take the role of MC.
The crocodile logo was designed by Victoria Jankowski. It was first used on the cover of Neon-komputadór, the first IT training manual for the Ministry of Foreign Affairs in East Timor which was printed and translated by the United Nations Development Programme. The crocodile represents the Timorese people and is the emblem of their land. The integrated circuit represents their independent connectivity to the wider world.
You can also find a political site that Lev subscribes to, The Isocracy Network, a synthesis of several progressive political orientations, and RPG Review which covers his interests in roleplaying and simulation games, including as editor of the namesake journal. This includes being the author of one very ironic RPG (Papers & Paychecks) and supplement (Cow-Orkers in the Scary Devil Monastery), a co-author of another (Fox Magic, author a supplement, Rolemaster Companion VI), as well as plot and character development in the computer game Cargo. He has also been a playtester for RuneQuest, Traveller, Basic Role Playing, and Eclipse Phase.
As a naturalistic pantheist with an interfaith perspective, he manages and contributes to the Lightbringers website which includes various addresses and essays on philosophy and religion. Recently he has taken up the role of University Outreach Officer for the International Society for Philosophers.
Finally, he also has a livejournalDreamwidth account, which will probably be quite boring to anyone who doesn't know him personally.
That's enough of me talking about myself in the third person like Cerebus The Aardvark.


 Way back in 2015 the University of Melbourne had a general-purpose high performance computer system called "Edward", which itself replaced an even smaller system called "Alfred", both named after the Kings of Wessex. Edward was a fairly typical machine for its vintage and, as is normal, when a system is being retired the main researchers were asked what should be different in the new system. What was also normal was their answers; more cores, faster CPUs, etc.
Way back in 2015 the University of Melbourne had a general-purpose high performance computer system called "Edward", which itself replaced an even smaller system called "Alfred", both named after the Kings of Wessex. Edward was a fairly typical machine for its vintage and, as is normal, when a system is being retired the main researchers were asked what should be different in the new system. What was also normal was their answers; more cores, faster CPUs, etc.